Do you feel bewildered by the tangle of Linux security tools? Rest assured—we’ve got you covered. This in-depth manual explores 50 key tools in great detail, offering an in-depth analysis of their advantages, disadvantages, and potential to improve your Linux security posture.
This is your one-stop shop for creating an impenetrable Linux fortress, regardless of your level of experience as a sysadmin or where you are in your security journey.
Vulnerability Scanners: Discovering Latent Vulnerabilities
Vulnerability scanners may be compared to your digital detectives, identifying vulnerabilities before bad actors can take use of them.
1. OpenVAS
OpenVAS: Security experts love this open-source powerhouse because it can be customized and gets changes often. OpenVAS looks through your systems for known security holes and gives you thorough reports that show you exactly what needs to be fixed right away. It’s very flexible and can be used for a lot of different scanning tasks.

Installation:
sudo apt update
sudo apt install openvas2. Nessus
Nessus is the best reader for businesses that is also easy for regular people to use. It has a huge library of vulnerabilities, can check everything, and reports easily. There are both free and paid versions of Nessus, but even the free version is a big protection improvement.
3. Nmap
This powerful tool does a lot more than just check ports. Nmap creates a map of your network, finds operating systems and services running on machines that are linked, and even finds holes in the security. You can think of it as having X-ray vision over your whole system. This lets you see where attacks could come from and find possible weak spots.

Installation:
sudo apt update
sudo apt install nmap4. Nikto
Nikto is antivirus software designed to scan your websites and web apps for harmful files, old software versions, and common mistakes that hackers love to take advantage of. Any business or group with a website needs to have this tool.
Installation:
sudo apt update
sudo apt install nikto5. OpenSCAP
OpenSCAP is a tool for handling security reviews, making sure systems are hardened based on best practices, and checking that they are compliant with industry standards. It is more than just a vulnerability checker. Businesses that need to meet certain security standards can use this useful tool.
6. Qualys FreeScan
Want to do a quick security check without buying a tool? With Qualys FreeScan, you can quickly find important risks to your web services and network infrastructure through a security review. For companies that want to improve their protection, it’s a great place to start.
7. Nexpose Community Edition

Nexpose Community Edition is the free version of Rapid7’s vulnerability management platform. It has powerful scanning tools, such as the ability to prioritize vulnerabilities and let you customize reports. Small and medium-sized businesses that want a complete and free risk management tool should look at this one.
Firewalls: Guarding the Gates of Your Digital Kingdom
Firewalls control the data getting into and going out of your network and keep out people you don’t want to be there.
8. Iptables
You can fine-tune network rules with this built-in Linux firewall, which lets you say exactly what data is allowed and what is banned. Iptables is very useful, but it can be hard to configure, especially for beginners.

Installation:
sudo apt update
sudo apt install iptables9. UFW (Uncomplicated Firewall)
As its name suggests, UFW makes managing firewalls easier with a simple set of rules and an easy-to-use command line tool. It’s great for people who want a strong but simple firewall but don’t want to learn how to use iptables.
Installation:
sudo apt update
sudo apt install ufw10. Firewalld
Firewalld is a customizable firewall server that lets you set up various configurations based on zones. Firewalld makes it easy to handle firewall rules for different network settings, such as public, internal, and trusted. This makes it a good choice for servers and complex network setups.
11. Shorewall
Developed for those in charge of handling large firewall rule sets, Shorewall offers a higher-level configuration tool that makes the process easier and lowers the possibility of errors. It works especially well for servers and gateways that handle a lot of traffic.
12. pfSense
You should think about pfSense if you want a powerful and flexible firewall system built on FreeBSD. It has a lot of features, such as VPN support, traffic shaping, attack detection, and an easy-to-use web interface for control.
Intrusion Detection and Prevention Systems (IDS/IPS): Proactive Defense Against Threats
IDS/IPS tools are the protectors and alarm clocks of your system; they immediately identify and stop suspicious behavior.
13. Snort
Snort, popular for its rule-based detection and real-time traffic analysis, is an open-source intrusion detection and prevention system. The hundreds of rules you can add to Snort enable proactive security monitoring by matching specific threats and alerting you to suspicious activities.
Installation:
sudo apt update
sudo apt install snort14. Suricata
Designed to function in high-performance settings, Suricata’s robust scripting features and multi-threading make it the perfect choice for networks with heavy traffic. Additionally, it offers greater visibility into network traffic by supporting cutting-edge technologies like TLS encryption inspection.

Installation:
sudo apt update
sudo apt install suricata15. Fail2ban
Fail2ban is a watchful watchdog that monitors log files for questionable behavior, such as repeatedly unsuccessful login attempts. Fail2ban guards your system against brute-force attacks by automatically blocking problematic IP addresses when it detects suspicious activity.
Installation:
sudo apt update
sudo apt install fail2ban16. OSSEC
This open-source host-based intrusion detection system offers extensive monitoring, including rootkit detection, file integrity checks, log analysis, and more features. You can implement OSSEC on a range of devices, such as servers, workstations, and embedded systems, to provide thorough threat detection across your infrastructure.
17. Security Onion
This Linux distribution includes a robust set of pre-installed security tools, such as Suricata, Bro, and Snort. For security analysts and companies seeking an easy-to-deploy solution, Security Onion is the perfect choice since it provides a centralized platform for network security monitoring and intrusion detection.
Security Auditing and Hardening Tools: Building an Impregnable Fortress
These tools serve as your system’s auditors of security, finding and assisting you in repairing any weaknesses in its defense.

18. Lynis
This open-source auditing tool checks systems thoroughly and gives suggestions for how to make them better. Lynis is a useful tool for thorough security reviews because it addresses a wide range of security issues, from configuration protection to vulnerability discovery.
Installation:
sudo apt update
sudo apt install lynis19. Tiger
This strong tool for security testing and attack detection helps you find possible risks and meet compliance standards. Tiger checks out your systems, looks at your configuration files, and makes thorough reports that show you what needs to be fixed.
20. Bastille Linux
For those who are new to security strengthening, Bastille Linux is the perfect program to start with. Hardening your Linux system is easy with this tool’s step-by-step instructions. You don’t need to know a lot about security to make your surroundings safe.
21. Tripwire
This file integrity monitoring tool helps find changes that aren’t supposed to be made to important system files. It warns you about possible malware attacks, illegal changes, and other bad things that could happen to your system and make it less safe.
22. Aide (Advanced Intrusion Detection Environment)
As with Tripwire, Aide (Advanced Intrusion Detection Environment) offers strong monitoring of file integrity. Aide lets you set different rules for each file and directory, so you have fine-grained control over which changes will send you alerts.
Log Management and Analysis Tools: Deciphering the Tales Your Data Holds

Log files, like a diary, keep track of everything that happens on your machine. These tools allow you to find hidden risks and learn useful things from that data.
23. ELK Stack (Elasticsearch, Logstash, Kibana)
The strong open-source stack ELK Stack (Elasticsearch, Logstash, Kibana) is a favorite for managing and analyzing logs from one place. Get logs from different places, use Logstash to sort and improve them, Elasticsearch to store and find them, and Kibana to see the data. ELK gives you a robust way to see what’s going on in your system and find strange things.
24. Graylog
Need a powerful log management tool that is also easy to use? Check out Graylog. Graylog is a great choice for open source. It has a simple interface for getting log data, looking at it, and showing it. There are also graphs, alerts, and links to different info sources in it.
25. Splunk
Splunk is a paid tool for managing and analyzing logs that lets you see your machine data in real time. Splunk is great at working with big amounts of data and has strong search, analysis, and display tools. Splunk is a paid option, but you can try it for free and get a free license with restricted features for smaller settings.
Security Information and Event Management (SIEM) Tools: Connecting the Security Dots

By aggregating and matching security data from many sources, SIEM systems provide a centralized security command center.
26. AlienVault OSSIM
Asset identification, vulnerability analysis, intrusion detection, and log analysis are among the complete range of security monitoring and management features offered by AlienVault OSSIM—open-source SIEM. AlienVault OSSIM provides a comprehensive picture of your security posture and supports efficient threat identification and response.
27. Security Incident Response Platform (SIRP)
Streamlining incident management, this open-source Security Incident Response Platform (SIRP) The Hive guarantees a disciplined and effective reaction by centralizing monitoring, documentation, coordination on, and reporting of security events.
28. MISP (Malware Information Sharing Platform)
Promoting cooperation by means of threat intelligence sharing between companies, MISP (Malware Information Sharing Platform) is an open-source tool. By letting you share and get knowledge about malware samples, attack indicators, and other security concerns, MISP helps you keep ahead of developing threats.
Network Security Tools: Shielding Your Digital Perimeter

You can monitor and safeguard your network against harmful activities and illegal access with the aid of these technologies.
29. Tcpdump:
With this robust command-line tool, you may see the data moving over your network in its unprocessed state as it gathers and analyzes network traffic in real. Understanding network behavior, spotting suspicious activity, and resolving network problems are all made possible with the help of tcpdump.
Installation:
sudo apt update
sudo apt install tcpdump30. Wireshark
Network traffic may be captured, filtered, and inspected more easily with the help of the well-known graphical network protocol analyzer Wireshark. An indispensable tool for network administrators and security experts, Wireshark supports a large number of protocols and provides sophisticated filtering and analysis capabilities.
Installation:
sudo apt update
sudo apt install wireshark31. Ettercap
There are both potentially harmful and useful applications for this set of network security technologies. Ettercap is helpful for penetration and security testing since it enables you to intercept, examine, and even alter network data on a local area network (LAN). When use Ettercap, exercise caution however, since it might be exploited for immoral purposes.
32. Kismet

Wireless network security is the area of expertise for Kismet. Wireless network detection, wireless traffic capture, and common wireless attack detection are all done by Kismet. For assessing the security of your Wi-Fi networks and spotting any weaknesses, it’s a priceless tool.
33. Ntopng
Network utilization is seen in real time with Ntopng, a high-speed network traffic analyzer. Using Ntopng, you can see comprehensive details about hosts, protocols, and network chats. This information helps you spot unusual traffic patterns, bandwidth-hogs, and other security problems.
Endpoint Security Tools: Building Defenses from the Inside Out

Endpoint security concentrates on protecting against attacks individual devices such servers, desktop computers, and laptops.
34. ClamAV
Open-source antivirus engine ClamAV offers consistent defense against malware, viruses, and other hazards. By scanning attachments, emails, and files for harmful material, ClamAV may assist to stop data breaches and infections.
Installation:
sudo apt update
sudo apt install clamav35. Sophos Antivirus for Linux:
Real-time protection for Linux computers comes from this free antivirus solution from Sophos Antivirus for Linux. It’s a great free antivirus choice as it offers heuristic analysis, automated updates, and on-demand scanning to identify and prevent known and unidentified hazards.
36. chkrootkit
Rootkits are meant to be covert, hence they are hard to find. Discovering these risks is the area of expertise for chkrootkit; it searches your system for known rootkit signatures and abnormalities pointing their existence.
Installation:
sudo apt update
sudo apt install chkrootkit37. rkhunter
Another great weapon for eradicating rootkits and other harmful software is rkhunter, which analyzes system file integrity, searches for unusual activities, and scans for known rootkit backdoors therefore offering a multi-layered protection against these sneaky dangers.
Installation:
sudo apt update
sudo apt install rkhunter38. AppArmor
AppArmor is a Linux Security Module (LSM) that enables application mandated access control. AppArmor limits apps to accessing only the resources they need, therefore stopping hacked programs from causing havoc on your machine.
39. SELinux (Security-Enhanced Linux)
Another strong LMS, SELinux (Security-Enhanced Linux), implements security rules defining how users and programs could interact with the system. Operating on the least privilege concept, SELinux greatly reduces the harm possible from any weaknesses.
Data Encryption Tools: Securing Your Sensitive Information
Constantly threatening are data breaches. These technologies protect your private data even in cases of incorrect hands.
40. GnuPG (GPG)
Strong encryption for files, emails, and other data is offered by the extensively used GnuPG (GPG) implementation of the OpenPGP standard. Using public-key cryptography, GPG lets you securely distribute data knowing only authorised people may decode and access it.
Installation:
sudo apt update
sudo apt install gnupg41. VeraCrypt
Must guard private information kept on your internal drive? VeraCrypt generates encrypted volumes, like effectively password-protected file containers. It offers on-the-fly encryption, hence once you unlock the volume, you may access your data transparently.
42. LUKS (Linux Unified Key Setup)
On Linux systems, LUKS (Linux Unified Key Setup) offers a consistent method to encrypt whole platter drives or single partitions. LUKS gives you freedom and control over the encryption of your data by supporting many encryption techniques and key management choices.
Password Management Tools: Taming the Password Jungle

Though maintaining them might be daunting, strong, unique passwords are really vital. Password managers improve your security while streamlining this chore.
43. KeePassXC
KeePassXC is an open-source password manager that encrypted database secured by a master password saves your passwords and other sensitive data. There are many platforms for KeePassXC that guarantees you may access your passwords anywhere.
44. Bitwarden
Another great open-source password manager, Bitwarden provides both free and premium models. It’s simple to handle and safe your credentials across devices thanks to cloud synchronization, two-factor verification, and secure password sharing.
45. LastPass
Popular commercial password manager LastPass provides subscription plans with sophisticated features like family password sharing and dark web surveillance on top of a free tier with simple tools. LastPass is a rather easy tool with plenty of capabilities.
Virtual Private Network (VPN) Tools: Tunneling Through the Dangers of Public Wi-Fi
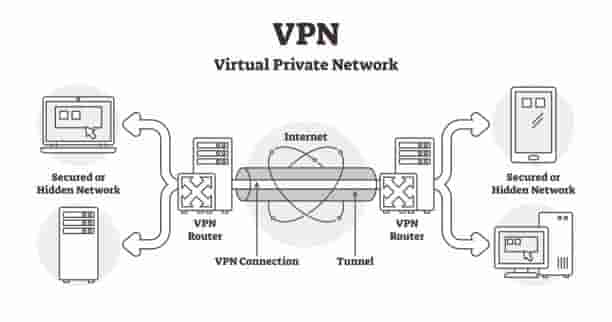
A virtual private network (VPN) encrypts all of your data sent over the internet, even while you’re using public Wi-Fi.
46. OpenVPN
Connect securely to distant networks or surf the web anonymously using OpenVPN, an open-source VPN technology and software that is widely used. You may customize OpenVPN to fit your needs, and it works with a wide range of systems.
Installation:
sudo apt update
sudo apt install openvpn47. WireGuard
Quickness, ease of use, and safety are the pillars of this cutting-edge VPN protocol called WireGuard. For both home and office networks, WireGuard is a great choice because to how simple it is to set up and launch.
Installation:
sudo apt update
sudo apt install wireguardOther Essential Security Tools: Rounding Out Your Toolkit
These tools defy easy categorization but are invaluable additions to your security arsenal.
48. John the Ripper
Acting like an ethical hacker, this password cracking tool lets you find weak points in your security posture and test the strength of your own passwords. Among the many cracking approaches John the Ripper uses are brute-force and dictionary assaults.
Installation:
sudo apt update
sudo apt install john49. Aircrack-ng
Aircrack-ng: Designed to evaluate Wi-Fi network security, this set of tools Helping you find and fix weaknesses in your wireless networks, Aircrack-ng can record wireless traffic, evaluate Wi-Fi security protocols, and even try to crack weak passwords.
50. Burp Suite
Web developers and security experts really must have this comprehensive platform for web application security testing. Burp Suite lets you find and take advantage of web application weaknesses so you may remedy them before attackers do.
Building Your Impregnable Fortress: A Continuous Journey
With the information and resources provided by this exhaustive list, you can fortify the security of your Linux environment. Always keep in mind that security is a continuous process, not a one-time event. To remain one step ahead of security threats, it is important to be informed about new developments, update your systems regularly, and continually adjust your security methods.
FAQ
Having discussed the tools, let’s now answer some often asked questions about Linux security!
General Linux Security
Q1: I’m new to Linux. Is it more secure than other operating systems?
Although Linux has a solid security reputation, no operating system is absolutely perfect. Its open-source character lets communities examine software, which sometimes speeds up vulnerability fixing. Still, regardless of your operating system, being educated and aggressive with security measures is really vital.
Q2: Do I really need to use all 50 of these tools?
Surely not! Your particular requirements, technical ability, and the system you want to protect will determine the correct tools. Start with the fundamentals: a powerful firewall (such as UFW), vulnerability scanner (such as OpenVAS), and an intrusion detection system (such as Snort) and then expand.
Q3: What are some simple steps I can take to improve my Linux security right now?
- Update often to This covers the system, programs, and security instruments itself.
- Robust passwords: Whenever at all feasible, turn on two-factor authentication using a password manager.
- Don’t utilize root unless absolutely required; follow least privilege.
- Regarding downloads and email attachments, be careful. Check the source before opening anything or clicking.
Tool-Specific Questions
Q4: What’s the difference between iptables, UFW, and Firewalld?
The most potent but also the most complicated tool available for exact control over network filtering is iptables.
- Simplifying fundamental firewall rules, UFW is a user-friendly front-end for iptables.
- Firewalld: With zone-based setups, provides more dynamic firewall administration.
Q5: I see OpenVAS and Nessus mentioned a lot. Which one is better?
- Free and open, fully configurable, and routinely updated OpenVAS is. Popular among security experts.
- Nessus: More approachable with first-rate reporting capabilities. Though it has restrictions, the free edition serves as a decent basis.
Q6: Why should I use a log management tool like ELK or Graylog?
Log files provide priceless details about the behavior of your system. These instruments serve you:
- Consolidate log information coming from many sources.
- Search and filter quickly across logs.
- Create alarms for unusual behavior.
- Make perceptive dashboards that show security patterns.
Q7: I’ve heard about SELinux but it seems complicated. Is it worth the effort?
Mandatory access control offers SELinux, protection-Enhanced Linux, a strong layer of protection. Although its learning curve is high, its ability to restrict the influence of hacked apps makes it well worth thinking about for critical systems.
Getting Help
Q8: I need help setting up or troubleshooting these tools. Where can I find support?
- Online communities: Excellent tools abound from Linux and cybersecurity forums and subreddits.
- Tool documentation: Official websites and documentation abound for most tools.
- If you handle sensitive information or complicated security concerns, don’t hesitate to consult experts.
Remember: security is not a destination; it is a continuous process. Never stop studying; be educated and watchful.